- Employees invite guests (either through the essentry Dashboard or a pre-processor system) and can assign access profiles to these guests. The employee can also specify if their guests can move around by themselves or if they must be escorted by the host.
- essentry sends an invitation email to the guests with a QR code that they can use to check-in at the essentry Kiosk when they arrive at the facility. The email can also contain other information and guide the guest through an Online Check-in to save time during the check-in or to report a wrong spelling of their name.
- When the guest checks in at the essentry self-service Kiosk and their identity is successfully verified, the Kiosk dispenses an RFID card. Thanks to the access control system integration the card holds the access profiles that the host specified during the invitation process as described under Integration and Synchronization.
- The host is informed about the guest’s arrival via email.
- If the host has specified that the guest must be escorted, the RFID card will not be activated yet until the host has confirmed the pick-up. The host pick-up process is not described in this document.
- The host and the security personnel can still add or remove access profiles afterward in the essentry Dashboard in case a permission was forgotten during the invitation (see screenshot below).
- When the guest is checked out, the RFID card will be deactivated, and all access profiles will be removed.
Integration and Synchronization
essentry’s access control integrations offer a two-way-synchronization:- Every door/lock and every access profile (a group of doors/locks) are loaded from the access control system and synchronized into the essentry system. This information is automatically kept up to date. This allows employees and security personnel to select these profiles easily from the essentry Dashboard or the Outlook integration.
- When a guest has successfully checked-in, essentry creates the person inside the access control system, assigns them the correct RFID card (that was dispensed at the Kiosk), and attaches the access profiles that were specified during the invitation. essentry can also update, disable, or remove the records from the access control system if they get updated in the essentry Dashboard or the guest has been checked out.
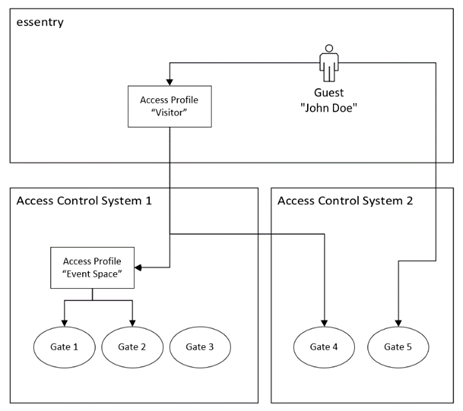
Multiple Access Control Systems
essentry can work with multiple access control systems and can offer a unified interface to all systems for employees and security personnel. The basic integration and synchronization work as described above.